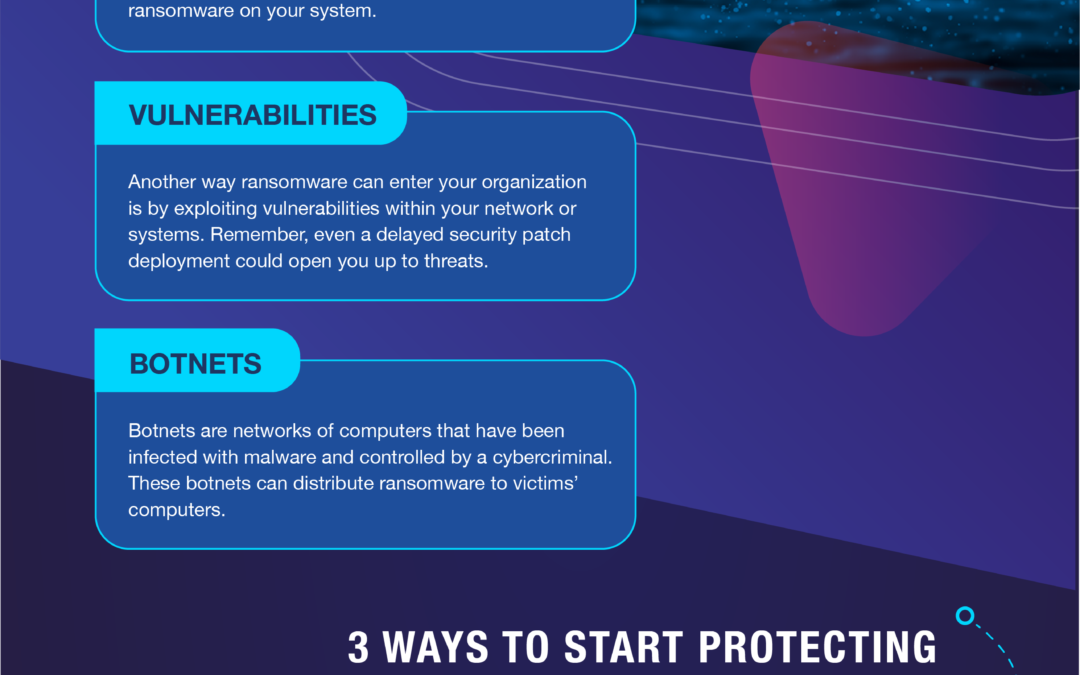
Why Passwords are Your Business’s Weakest Point
In today’s world, safeguarding your organization’s online assets is critical. Unfortunately, poor “password hygiene” practices by some employees cause problems for many businesses, leaving them vulnerable to hackers.
Cybercriminals are constantly trying to find new ways to break into business systems. Sadly, too often, they succeed thanks to weak passwords. In fact, nearly 50% of cyberattacks last year involved weak or stolen passwords.* This calls for businesses like yours to step up and take password security seriously and implement strong password policies.
Fortunately, there are a few best practices that you can follow to protect your business. Before we get into those, here are the top 10 most common passwords available on the dark web that you should avoid at all costs:
- 123456
- 123456789
- Qwerty
- Password
- 12345
- 12345678
- 111111
- 1234567
- 123123
- Qwerty123
Password best practices
By simply making your team aware of password best practices, they can significantly improve your cybersecurity.
Use a password manager
One of the most important things to keep your passwords safe is to use a password manager. A password manager helps you create and store strong passwords for all your online accounts. Password managers can also help you keep track of your passwords and ensure they are unique for each account.
Implement single sign-on (SSO)
Single sign-on is a popular password solution that allows users to access multiple applications with one set of credentials. This means that you only need to remember one password to access all your online accounts.
While SSO is a convenient solution, remember that all your accounts are only as secure as your SSO password. So, if you’re using SSO, make a strong, unique password that you don’t use for anything else.
Avoid reusing passwords on multiple accounts
If a hacker gains access to one of your accounts, they will try to use that same password to access your other accounts. By using different passwords for different accounts, you can limit the damage that hackers can cause.
Make sure to never to jot down your passwords on a piece of paper and instead depend on a safe solution like using a password manager.
Use of two-factor authentication (2FA)
One of the best ways to protect your online accounts is to use two-factor authentication (2FA). In addition to your password, 2FA requires you to enter a code from your phone or another device. Even if someone knows your password, this method makes it much more difficult for them to hack into your account.
While 2FA is not perfect, it is a robust security measure that can assist in the protection of all of your online accounts. We recommend that you begin using 2FA if you haven’t already.
Don’t use the information available on your social media
Many people use social media to connect with friends and family, stay up to date on current events or share their thoughts and experiences with others. However, social media can also be a source of valuable personal information for criminals.
When creating passwords, you must avoid using information easily obtainable on your social media accounts. This includes your name, birth date and other details that could be used to guess your password. By taking this precaution, you can help keep your accounts safe and secure.
Healthcare Practice IT can help you
As cyberattacks become more sophisticated, you may not be able to devote sufficient time and effort to combat them. Healthcare Practice IT can ensure your team creates strong passwords, stores them securely and changes them on a regular basis.
Schedule a no-obligation consultation with us today to learn more about how we can help protect you from poor password hygiene.
Now that you know how to keep your passwords safe, download our infographic by clicking here to learn how to keep your email inbox safe.
Source: * Verizon DBIR 2022
More blog articles
Minimizing Cyber Supply Chain Risks through Effective Vendor Selection
Cyber supply chain risks refer to the threats that arise from the use of products or services provided by external vendors in an organization’s IT infrastructure. These risks can originate from various sources such as malware-infected software, compromised hardware, or unreliable service providers.
Co-Managed IT for Healthcare Organizations
Co-managed IT is a service model that can help healthcare organizations
improve their IT infrastructure while minimizing risk and cost. By partnering
with a co-managed IT provider that specializes in healthcare, organizations
can ensure that their IT systems are secure, compliant, and optimized for
performance. Learn more about the benefits of co-managed IT for
healthcare organizations and how to implement it in our latest blog post
Co-Managed Healthcare IT Myths
Co-Managed IT Services have emerged as a viable solution for healthcare organizations to leverage the benefits of IT without breaking the bank. In this article, we debunk some of the most common Co-Managed IT myths and explore the benefits of partnering with a Managed Service Provider.